$50 Million Gone in Seconds: The Anatomy of an Address Poisoning Attack
By Coin Frontier Research Team
Executive Summary
On December 20, 2025, the cryptocurrency world witnessed one of the most devastating "fat finger" errors in history. A sophisticated investor, often referred to as a "whale," lost $50,000,000 USDT in a single transaction. This was not a result of a smart contract exploit, a leaked private key, or a brute-force hack. It was the result of a psychological exploit known as Address Poisoning.
This report provides a forensic analysis of the incident, explaining exactly how attackers weaponize the "safety habits" of experienced users. We dissect the technical mechanics of vanity address generation and provide a definitive guide on how to secure your assets using hardware solutions like Ledger and Tangem.
Case Study: The $50 Million Mistake
Based on on-chain data and reports from security analysts (SpecterAnalyst, Lookonchain), we have reconstructed the timeline of the event.
The Actors
The Victim: Identified by the wallet prefix 0xcB80.... This entity holds significant capital and is a prime target for automated monitoring.
The Intended Recipient: The victim's own secondary wallet.
Target Address Fragment: 0xbaf4b1aF...B6495F8b5
The Attacker: An automated bot cluster scanning the mempool for high-value transfers.
The Timeline of Destruction
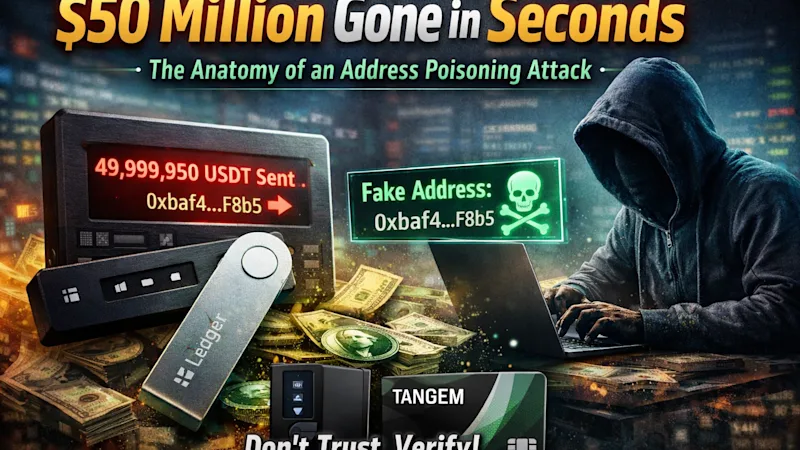
The Safe Start (The Test): The victim intended to move $50M USDT. Following standard security best practices, they first sent a test transaction of 50 USDT to their destination address (0xbaf4...5F8b5). The test was successful.
The Poison Injection: The attacker's bot detected this 50 USDT transfer. Using high-speed GPU clusters, the attacker immediately generated a "lookalike" address.
Attacker’s Spoofed Address: 0xBaFF......8f8b5
The attacker then sent a 0.005 USDT (or tiny dust) transaction from this spoofed address to the victim (0xcB80...).
The Fatal Error: The victim returned to their wallet to send the remaining 49,999,950 USDT. Trusting their "Recent Transaction History," they saw the entry at the top of the list.
They checked the first 4 characters: 0xbaf4 (Match).
They checked the last 5 characters: F8b5 (Match).
Assuming it was the address they just used, they copied it and hit send.
The Aftermath: The $50 million was sent to the attacker. Because blockchain transactions are immutable, the funds were lost instantly.
The Mechanics: How to "Clone" an Identity
To understand how an attacker can generate a matching address in seconds, we must look at the cryptography.
The Mathematics of Vanity
Ethereum addresses are 40-character hexadecimal strings (derived from the Keccak-256 hash of the public key).
Full Collision: Generating an address that matches completely is mathematically impossible ($1$ in $16^{40}$).
Partial Collision: Generating an address that matches just the first 4 and last 4 characters is trivial.
Using a tool like Profanity2 and a modern GPU (e.g., NVIDIA RTX 4090), an attacker can generate millions of addresses per second.
The attacker does not need to hack your wallet. They simply need 4 seconds to create a mask that looks like your destination, and then they rely on your brain to fill in the blanks.
The Psychological Vulnerability
This attack works because it exploits System 1 Thinking (fast, intuitive processing).
Truncation Blindness: Most wallets (MetaMask, Trust Wallet, etc.) shorten addresses to 0x1234...ABCD. This hides the middle 30 characters—the exact place where the difference lies.
Trust in History: Users implicitly trust their "Recent Transactions" tab as a log of their actions. Poisoning pollutes this log with external actions, tricking the user into copying a hostile address.
Defense Architectures: Hardware Solutions
Software wallets are vulnerable to UI truncation and clipboard hijacking. Hardware wallets provide a physical "Source of Truth."
The Ledger Ecosystem: "Trusted Display"
Ledger devices (Nano S Plus, Nano X, Stax) feature a dedicated screen that is isolated from your computer's malware.
The Defense: When you send a transaction, the address scrolls across the physical device screen. You must verify the full string here. Even if your computer clipboard has been poisoned, the device will show the actual destination.
Zero-Value Hiding: Ledger Live has updated its software to automatically hide "0 Value" transactions, filtering out the most common form of poisoning attacks.
Coin Frontier Offer:
Secure your assets with a Ledger and receive a $20 - $25 Bitcoin Bonus via the referral program.
The Tangem Ecosystem: "Smart Card Security"
Tangem offers a credit-card-shaped hardware wallet that uses NFC and a mobile-first approach.
The Defense: Tangem relies on a clean mobile interface. The app allows users to "Hide" specific tokens or suspicious transactions. If you receive a "dust" transaction or a fake token, you can toggle its visibility off, preventing you from accidentally clicking it in the future.
Address Book: Tangem is rolling out features to save trusted addresses, reducing the need to ever copy from history.
Coin Frontier Offer:
Get a 10% Discount on Tangem Hardware Wallets.
Official Link:(https://tangem.com/invite/AK9PPA)
Discount Code: AK9PPA
Survival Guide: 3 Rules to Prevent Loss
If you hold crypto, you must adopt these rules today.
Rule 1: The "Address Book" Mandate
Never copy an address from your transaction history. It is a public log that anyone can write to. Always copy from a saved "Address Book" or the original source (e.g., the exchange deposit page).
Rule 2: Check the "Middle Bits"
Attackers can easily match the edges (0x1234...ABCD). They cannot match the middle. When verifying an address, ignore the start/end and check 4 random characters in the center.
Real: ...833D...
Fake: ...944E...
Rule 3: The "Clean Slate" Protocol
If you send a test transaction, wait for it to arrive. Then, do not use the "Repeat Transaction" button. Go back to the source and copy the address again. The attacker is counting on you being lazy during the second, larger transfer.
Conclusion
The loss of $50 million is a stark reminder that in the world of self-custody, attention is your only insurance. Address poisoning is not a hack of the blockchain; it is a hack of your attention span. By using hardware wallets like Ledger or Tangem and verifying the full address string on a trusted display, you can render this attack useless.
Disclaimer: The wallet addresses mentioned (0xcB80..., 0xbaf4...) are based on public reports of the incident. Full 42-character strings are redacted in this report to prevent accidental interaction. Always verify addresses from your own trusted sources.


![[Web3 Native] Create Instant Link Pages with Google! Introducing "cryptolinks.space"](https://images.ctfassets.net/wv6s970ktz13/6U7eMUOuQ0NqxgADqaF3fg/b84d540edc4900ffe5aafbf5c748f334/Gemini_Generated_Image_mb6z0zmb6z0zmb6z.png?fm=webp&w=128&h=128&fit=fill&q=75)

